- Introduction
- ACI Basics
- Access Policies
- ACI VMM Integration
- Tenants
- Day 2 Operations
- Endpoint Security Group
- ACI Segmentation
- Nexus Dashboard
- Orchestrator
- Insights
- Conclusion
- References
Many people, upon entering the fray of ACI, are wondering why access policies. In
the end, every network engineer has actually been working with the idea of access policies;
only they have been defined as text in a file as command lines, all under the interface of a device.
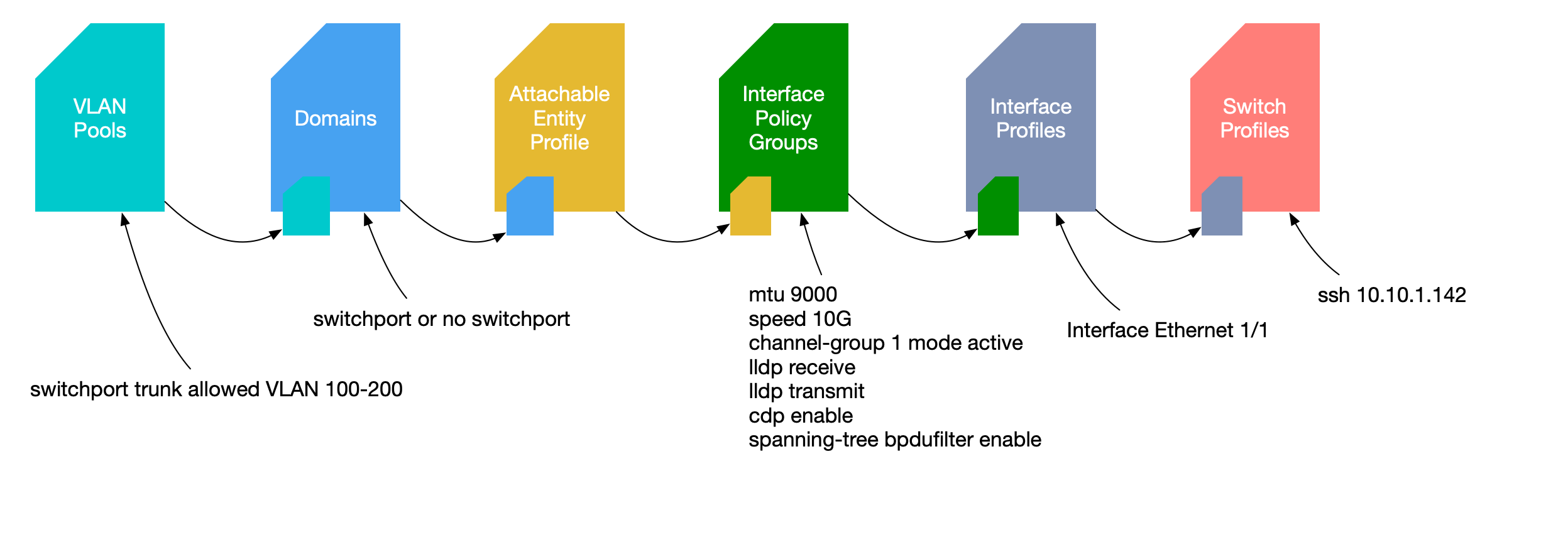
Since everything in ACI is based on programmatic objects, instead of having every interface
defined as a single object with properties, you can really take advantage of having
object inheritance that allows for policy re-use. While this is a difficult concept
to grasp, fabrics with 400 switches could use a ton of help in regards to how they are
configured in a way that enables efficiency.
For example, in fabrics that have racks that are identical (say 30 servers/rack), the
policies could be constructed in such a way that switch policies could inherit these
access policy definitions after creating them for one rack and re-using the same policies for many other
racks.
For this lab we will show you how create this structure of access policies and utilize
some wizards that Cisco has constructed to assist you in the process.
Continue to the next section where you will start building your access policies.


