As of ACI 5.0, Endpoint Security Groups (ESGs) are the new network security component in Cisco ACI.
Although the endpoint groups (EPGs) have been providing the network security in Cisco ACI, EPGs have to
be associated to a single bridge domain (BD) and used to define security zones within a BD. This is because
the EPGs define both forwarding and security segmentation at the same time. The direct relationship between the
BD and an EPG limits the possibility of an EPG to spanning more than one BD. This limitation of EPGs is resolved
by using the new ESG constructs.
Endpoint Security Groups
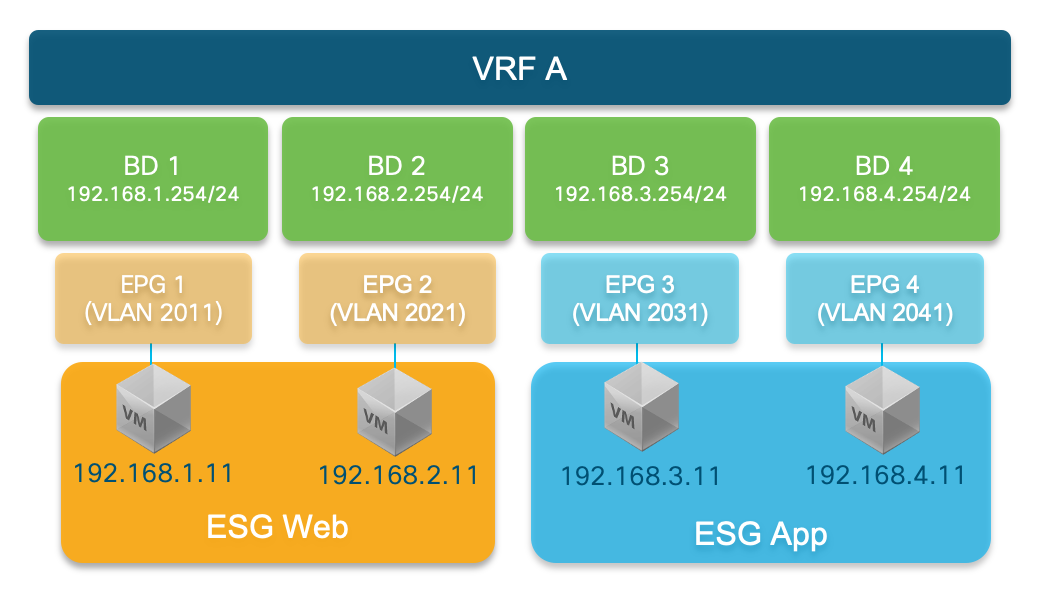
The diagram below represents the logical view of a VRF that contains multiple bridge domains and
their associated EPGs in a 1:1 relationship, and shows how ESGs can group endpoints from different
bridge domains/subnets and allow connectivity without the use of contracts across EPGs. Hence, the
primary benefits of ESGs are simpler contract configurations and policy TCAM (contract rules) usage optimization.
An ESG is a logical entity that contains a collection of physical or virtual network endpoints. In addition,
an ESG is associated to a single VRF instead of BD. This allows the definition of a security zone that is
independent of the BDs. Just as the EPGs divide a BD into security zones, the ESGs divide the VRF into security zones.
The EPG policy embeds both forwarding and security logic. For example, an EPG provides not only a security zone
based on VLAN, but also a VLAN binding on leaf node interfaces. Also, a contract on the EPG is used to enforce
the security and determine which leaf nodes the BD subnet should be deployed on, and which subnets to be leaked to
which VRF in the case of VRF route leaking (i.e. shared service). On the contrary, an ESG is used only to enforce
security using the contracts while the forwarding logics are handled by other components. With an ESG, the routing
logic such as BD subnets deployment and VRF route leaking are moved to VRF level. The VLAN binding on leaf node interfaces
are still handled at EPG level.
An ESG is a security construct that has certain match criteria to define which endpoint belongs to the ESG,
and uses contracts or policies to define the security stance. The match criteria are called the ESG selectors
that are based on attributes, such as an IPv4 or IPv6 address spanning across BDs in the associated VRF.
The contract usage in the ESGs is the same as the EPGs. Endpoints that belong to the same ESG can communicate
without the need for a contract. To enable communication between endpoints that belong to different ESGs, you need to
configure contracts between the ESGs. For the communication with devices outside of the Cisco ACI fabric, you need to
configure a contract between the L3Out external EPG and the ESG. You can also use a Layer 4 to Layer 7 service graph in
conjunction with a contract between the ESGs. However, contracts between an EPG and an ESG are not supported.


