- Introduction
- ACI Basics
- Access Policies
- ACI VMM Integration
- Tenants
- Day 2 Operations
- Endpoint Security Group
- ACI Segmentation
- Nexus Dashboard
- Orchestrator
- Insights
- Conclusion
- References
As discussed in the previous section, one of the biggest values of ACI is the ability by default to established a White Model Policy where
End-Point Groups (EPG) are not able to communicate with each other unless the admin configures a policy. This works very well between (EPG),
but customers were asking us what ACI could do in order to stop communication within EPGs. Keep in mind by default every
End-Point (EP) that it is part of the same EPG is able to freely communicate with eachother.
Here are some of the features that ACI has in order to stop communication between EPs. It is important to also understand the use case for each
feature. These features are very powerful if customers want to really take advantage of the Security Features ACI has.
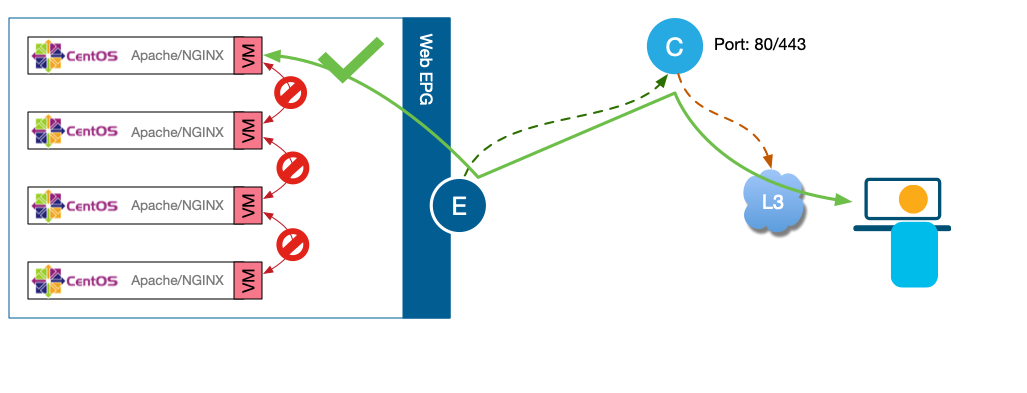
Intra-EPG Isolation
Intra-EPG Isolation allows the user to defined a policy in ACI where every EP within the same EPG or uSeg to communicating with eachother.
This feature is very similar to the Private VLAN concept that we have been supporting for years. Some of the use cases for Intra-EPG Isolation
are the following:
-
Storage Devices: Customers may define a Storage EPG where the Storage Arrays don't need to communicate with eachother.
-
Virus Spread: Customer can turn on this feature very fast in order to prevent Virus spreading to order devices.
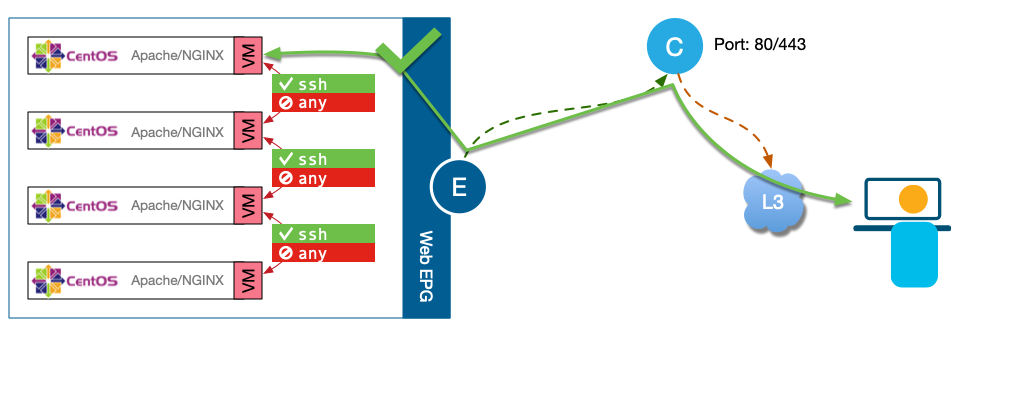
Intra-EPG Contract
Intra-EPG Contract is the ability to "relax" the Intra-EPG Isolation concept. Where in Intra-EPG Isolation none of the EPs are able
to communicate with each-other. With the Intra-EPG Contract feature, EP's are allow to communicate with each other based on policy. For example an user
may have an EPG called WEB where the webservers are located, in this particular case the user only want the webservers to communicate
with eachother only in certain protocol like keepalives or ssh. This feature provides the flexibility for certain users while keeping the
security parameters.
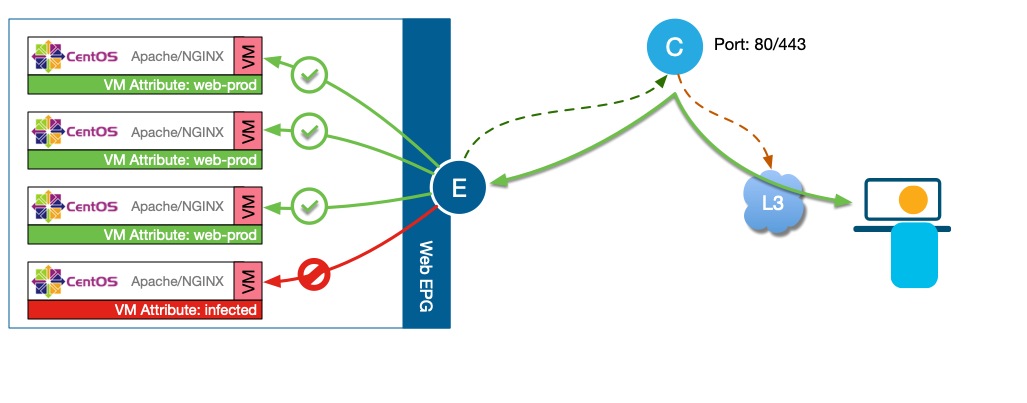
Network and Virtual Machine Based Attributes
Network Based Attributes allows the user to defined policies based on IP address filter and/or MAC address filter. For
Virtual Machines Based Attributes, the user defines the policy in vCenter attributes for examples VMM Domain, Operating
System, Hypervisor Identifier, Datacenter, VM Identier, VM Name, vNIC domain name, Custom Attribute and Tag.
The ability of ACI to provide support for Custom Attributes and Tag allows the user the flexibility to segment their
workloads based on these tags. For example, you may want to segment the VMs in the EPG WEB between prod and dev.
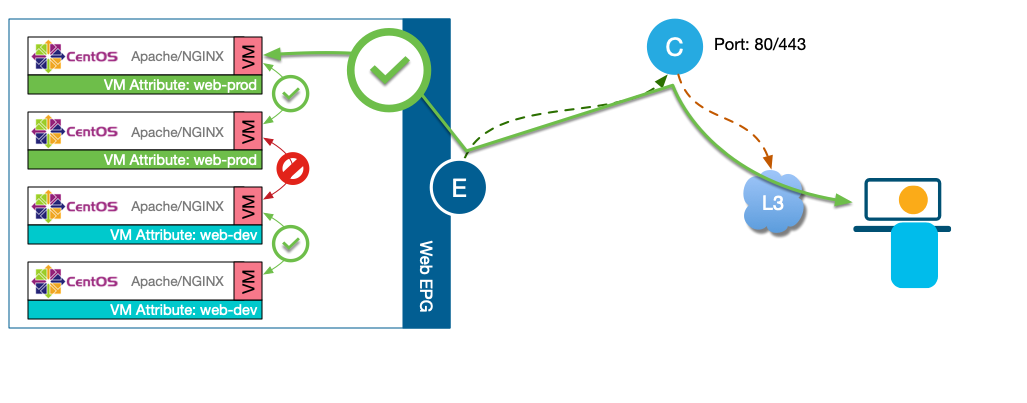
Another
use case that a lot of customers are leveraging these Attributes and TAG is to identified workloads that are infected and move
them to a quarantine uEPG.